Essential Network Protocols You Need to Know
Network protocols are like a rulebook that outlines how data moves gets received and gets handled in a computer network. They play a role in allowing different devices and software to effectively communicate and share information. The functioning of the internet and other computer networks would be impossible without these protocols. Let’s explore some aspects of network protocols;
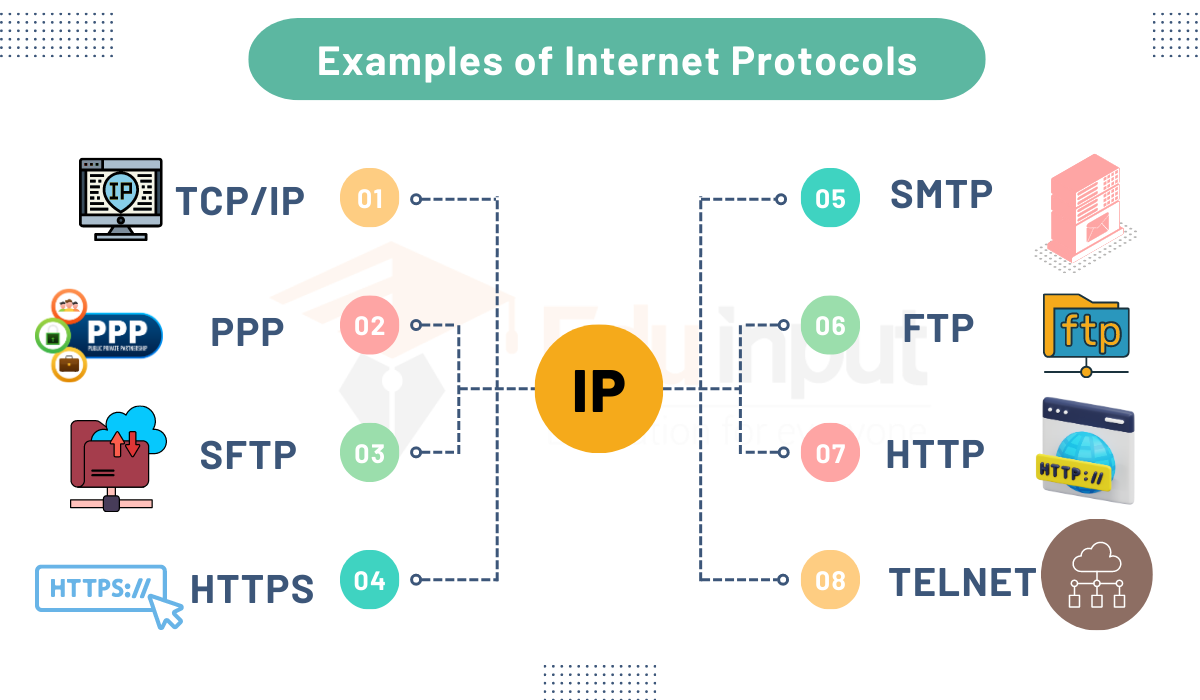
1. HTTP (Hypertext Transfer Protocol): used to send resources via the World Wide Web, such as web pages. It is the basis for web browsing and acts at the application layer.
2. HTTPS (Hypertext Transfer Protocol Secure): an HTTP extension that secures data transmission between a web browser and a web server using encryption (often TLS or SSL), protecting data confidentiality and integrity.
3. FTP (File Transfer Protocol): used to move files over a network between a client and a server. For safe file transfers, it includes two modes: FTP and FTPS (FTP Secure).
4. TCP (Transmission Control Protocol): A reliable and connection-oriented transport layer protocol responsible for ensuring that data sent from one computer to another arrives intact and in the correct order.
5. IP (Internet Protocol): a protocol at the network layer that provides the addressing and routing frameworks for transmitting data packets between devices via the internet or other IP-based networks.
6. UDP (User Datagram Protocol): A connectionless, compact transport layer protocol that prioritizes real-time or low-latency communication over reliability in applications. It is frequently employed for online gaming and streaming media.
7. SMTP (Simple Mail Transfer Protocol): between email clients and email servers for the purpose of sending email messages. The delivery of email messages to their intended recipients is outlined by SMTP.
8. SSH (Secure Shell): a secure network protocol used for secure file transfers between a client and a server as well as secure remote access. SSH provides authentication while encrypting the connection.
9. POP3 (Post Office Protocol version 3): a technique for retrieving emails from mail servers that email clients can use. Typically, it is used to download messages to a local device while keeping a copy on the server.
10. IMAP (Internet Message Access Protocol): IMAP is a different email retrieval protocol that enables email clients to manage and access email messages kept on a distant mail server. It is made to synchronize email between many devices.
In the interconnected world of contemporary computer networks and the internet, these protocols serve essential roles in facilitating a wide variety of network services and applications, assuring both efficiency and security. They serve as the essential building blocks of the complex system that supports digital communication, allowing for everything from file transfers and web browsing to email communication and real-time data streaming while preserving the accuracy, dependability, and integrity of data transmissions.
