Technology
The Future of Smart Interfaces: AI Meets IoT
The Future of Smart Interfaces: AI Meets IoT AI and IOT are most probably concepts you all know now. But when these two are in an intersection what will happen? The fusion of IOT and AI can be referred to as AIOT (Artificial Intelligence of Things). By using AI integration, the ability of IOT network…

Getting Started with Amazon Web Services (AWS)
Welcome to the world of cloud computing! If you’ve ever wanted to run a website, build an app backend, or deploy a full-stack system without investing in physical infrastructure, Amazon Web Services (AWS) is likely where you’ll begin. AWS is a cloud platform offering a massive collection of tools and services—everything from virtual servers to…

Planning to Start with Web Development: A Beginner’s Roadmap
In the starting days when I came to Web development, I had no small bit of idea what I was getting into. I just knew I wanted to develop something a website, app like something that we can see on the internet. So, like many beginners, I searched on YouTube and Google “How to become…

Frontend Web Development Trends in 2025
Frontend web development is evolving rapidly, and in 2025, several key trends are shaping how websites and applications are built. Expect frontend development to be heavily influenced by AI, with tools and frameworks leveraging machine learning for enhanced user experiences, performance, and development workflows, while accessibility and sustainability will also become core priorities. These are…
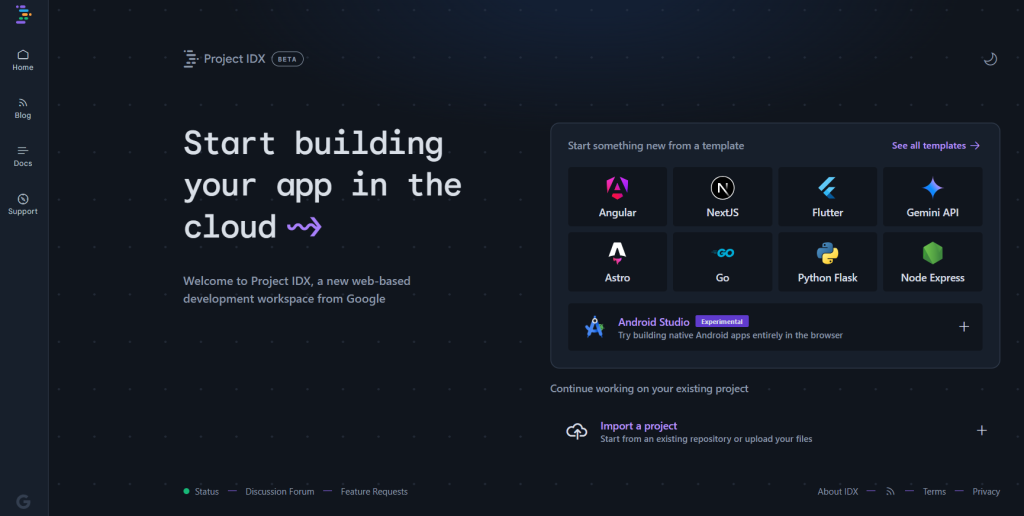
Project IDX
Are you a developer who loves experiencing new tools? then you may already know Project IDX by Google. If not, let’s get to know about that together. Imagine being able to code for the web, Android, and IOS all from your browser with no need of heavy setups, no installing dependencies, and no more saying,…
SEARCH GPT
A new way to use Search on the web Is here. Search GPT is the new innovation by OpenAI meant to improve the current way we search on the internet. Unlike Google and Bing, they only give a list of links when we search for anything. Search GPT uses AI conversant and gives the answer…
CI/CD & GitHub:Streamlining Software Development and Deployment
GitHub, a version control and collaboration platform where developers can store, manage, and track changes to their code. It is based on Git, which is a distributed version control system also designed by Linus Torvalds (the creator of Linux). GitHub brings in an online interface and extra tools for teams to coordinate on creating software development projects. Key…

Generative AI in Web Development: The Future is Now
Generative AI introduces a new method for web development which modifies the entire process of website designing and coding and performance optimization. AI-powered tools have transformed the creation process through automated UI/UX design together with content generation functions to optimize search engine results which speeds up developer creation of custom web environments. The future has…
As a web developer, what are the important things to learn?
As a Web Developer, you should start with basic languages of the trade – HTML, CSS, and of course JavaScript. HTML structure, CSS styles ,Bootstrap are also considered important to be known as it allows for easier and responsive layouts. HTML structure , CSS styles, and frameworks like Bootstrap for efficient, responsive designs. Strengthening these…
Web3 Identity and Security: The New Frontier of Digital Authentication
By now, most of our lives are tied to the digital world, and in most cases, using blockchain technology and decentralised systems, the idea of managing identity is being revolutionised. Web3 identity and security platforms are proven to be the solution to those problems of data ownership, privacy, and identity authentication. Favoured as it is…
- 1
- 2


