What Is iptables and How to Use It?
What Is iptables and How to Use It?
Have you ever wondered how the internet works? How does data travel from one computer to another seamlessly, navigating through a maze of networks? The answer lies in the intricate world of IP tables. But what are IP tables, and why are they so important?
Imagine the internet as a vast network of interconnected roads, with data packets zipping back and forth like cars on a highway. Now, think of IP tables as the traffic cops of this digital realm. They control the flow of data, deciding which packets are allowed to pass through and which are blocked at the gate.
But how do IP tables work their magic? At their core, IP tables are a firewall system built into the Linux operating system. They act as a barrier between your computer and the outside world, filtering incoming and outgoing traffic based on a set of predefined rules.
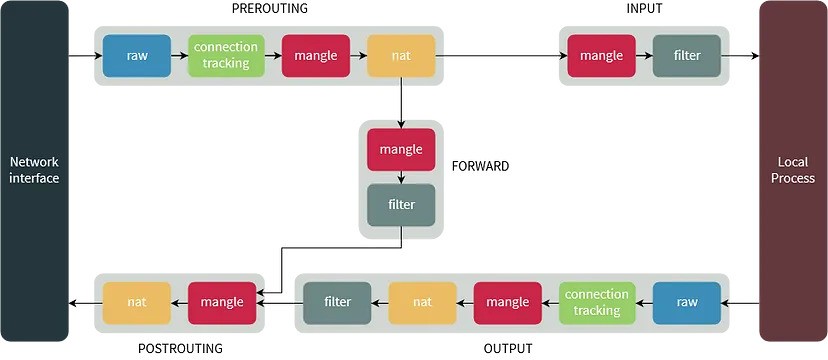
Think of these rules as a set of instructions that tell the IP tables what to do with each packet of data that comes its way. For example, you can create rules that allow certain types of traffic, such as web browsing or email, while blocking others, such as malicious attacks or spam.
But the power of IP tables doesn’t stop there. They also have the ability to perform network address translation (NAT), which allows multiple devices on a local network to share a single public IP address. This is crucial for conserving IP addresses and improving network security.
So, how can you harness the power of IP tables for yourself? Fortunately, you don’t need to be a computer genius to get started. With a basic understanding of Linux commands and a little patience, you can begin crafting your own firewall rules and protecting your system from unwanted intruders.
Start by familiarizing yourself with the syntax of IP tables commands. These commands allow you to create, modify, and delete rules, as well as view the current state of your firewall. Experiment with different rules and see how they affect the flow of traffic on your network.
But remember, with great power comes great responsibility. Misconfiguring your IP tables can have serious consequences, potentially leaving your system vulnerable to attack. Always double-check your rules and test them thoroughly before putting them into production.
Source: Internet
